Biometric Security: How Secure Is It Really?
Link Copied
What is biometric security, and is it really as secure as they say? This type of security used to be so advanced, it only appeared in James Bond movies. However, technology has come a long way and you may already be using biometric security in your everyday life.
In this article, you'll learn about what biometrics is, different types of biometric security options, as well how secure they are and how they are used.

What is Biometric Security?
Biometric security is a system that gives access only to specific people, rather than to specific passcodes or devices.[1] It uses body measurements and calculations for the person. These biometric methods can either replace or bolster traditional methods of security, such as a passcode, a PIN, or a dual-factor authentication method (such as pushing a button on your phone to access a website on your computer).
Types of Biometric Security Options
Some examples of biometric security options would be a retinal scanner, iris scanner, hand and finger geometry scanner, fingerprint lock, and facial scanner.[2] We'll cover the basics of these types below, as well as their pros and cons and how they are typically used.

Retinal Scan
A retina scan is a way of securely verifying a person's identity. A retina is the layer at the back of the eyeball. Like a fingerprint, each person' retinas are different and are the same throughout their lives. A retina scanner uses low-intensity light to look at the unique patterns on the blood vessels of the retina to certify who a person is.
Pros and Cons of Retinal Scan
Retina security scans are very accurate and secure, as it looks at unique patterns of a person's retinas and records them on video. It's hard to hack this type of security scan, which is a good thing. However, there are cons. Because of its advanced technology, a retina scanner is typically quite expensive. Some also believe it poses a health risk to the person being scanned.
How is Retinal Scanning Used?
Because of its expense, you may not see these often, however they are very useful when a high level of security is needed. That's why retina scan devices can be used for military, corrections, high-level government, and similar security clearances. An eye doctor or specialist will also use a retina scan to test the health of the eye, checking for issues such as diabetic retinopathy, glaucoma, age macular degeneration, and detached retina.

Iris Scan
An iris scan uses infrared light to looking at the unique pattern's in a person's irises in order to confirm a person's identity. The iris is the colored portion of a person's eye, with the pupil in the center. The iris lets light into the eye and controls the pupil. Like the retina, each person's iris is unique and has patterns that set them apart.
Pros and Cons of Iris Recognition
Iris scan recognition is extremely accurate, since everyone's irises are unique and don't change as people age. For this reason, it's hard to hack this type of security recognition. Another pro is that it is more sanitary since no physical contact is required, as the iris can be captured from a distance.
Iris recognition could have a major con, however, because of a potential security risk. Some they believe that if there is a national database of people's irises, people could be tracked without their knowledge.
It's a common misconception that iris scans can be damaging to your health. However, they are designed to not scan for more than 10 seconds or scan if you are too close.
How is Iris Recognition Used?
Right now, iris scanners are used for people to access certain devices such as mobile phones, border defense and a national citizen ID program, as well as gaining access to organizations.
Iris Scanner Security on Laptops
Outside of certain moblie phones and government/business security, iris scanning isn't used a lot. But that could possibly change. There is a device that can connect to a laptop via USB that uses a wand to scan the iris. Of course, your laptop could still be stolen, but without access via your unique iris, the criminal will be hard-pressed to access what's on the laptop.
Difference Between a Retinal Scan and an Iris Scan
Quite simply, both a retinal scanner and an iris scanner take rapid photos of the eye, but a retinal scanner takes photos of the retina while an iris scanner takes photos of the iris. Both the iris and the retina have unique patterns that are different even in identical twins. There are, however, some differences in the functionality of each type of scan.
The most important difference between a retinal scan and an iris scan is probably the convenience and the non-invasive process of the iris scan.[5] While a retinal scan requires a person to put their eye up to an eye piece for about thirty seconds,[6] an iris scan only requires a quick snapshot of the eye and does not require a person to put their eye up to any eyepiece whatsoever. For this reason, a retinal scan is considered invasive, while an iris scan is not, and more people are willing to submit to an iris scan than to a retinal scan.

Face Scan
Most people who have Googe Photos and/or a newer iPhone already know that facial recognition is not an imaginary thing of science fiction movies -- it's real and it's being used every day. A face scan is a type of biometric security that uses mathmatical patterns of the face to store that person's unique face identity.
Pros and Cons of Facial Recognition
Facial recognition make signing into your iPhone as simple as looking at the screen, plus it makes categorizing your Google Photos way quicker than doing it by hand. It's also more sanitary, since you don't have to touch anything for a face scan. Facial recognition is typically a quicker security verification than other methods like retina scan.
While facial recognition is useful, there are some flaws. It's not failsafe by any means. It can be hacked, as those with iPhones and Google photos already know. Sometimes kids will try to use their parents' photos to sign into their phones, and when you're categorizing Google photos there can be confusion between similar looking faces. Some argue that face scanners are biased according to race, plus people worry about their privacy if the government has access to facial recognition systems.
How is a Face Scanner Used?
Facial recognition technology is used in many different ways, including making most anything more secure such as medical records, retail stores, etc. Face scans are also used in law enforcement, which can use facial scan technology to try to locate people.
Difference Between a Face Scanner and Retinal or Iris Scanners
A face scanner looks at the shape of the entire face, while a retinal or iris scanner focuses only on the eye. Face scanners are less accurate than iris or retinal scanners, because face shape is not a completely unique characteristic the way that iris and retinal patterns are. However, face scanners can work from a much greater distance, meaning that they work very well for surveillance purposes because they can pick out a particular face from a crowd using facial recognition AI.[7]

Hand and Finger Geometry Scanner
A hand and finger geometry scanner is not dealing with fingerprints at all. While it does scan all of the fingers, it does not analyze any of the fingerprints.[3] The hand and finger geometry scanner is simply dealing with the size of the hand, the length and width of each finger, and the shape of the hand as a result of the finger sizes.[4]
A fingerprint lock, on the other hand (no pun intended), does not deal whatsoever with the size or shape of the hand or fingers, but rather picks up and analyzes the fingerprint of one particular finger. (Although most fingerprint locks can register more than one fingerprint to allow access to more than one person— or more than one finger of the same person— they still deal with only one fingerprint at a time).
Pros and Cons of Hand and Finger Geometry Scanner
What's great about this type of biometric security technology is that it can handle dirty hands, it can see the features it needs to even with a low-res image of the hand, plus it doesn't need a lot of data storage to operate (for example, a device can store over 40,000 biometric templates of different people).
Unfortunatley,hand and finger geometry scanning can be expensive, plus people worry about privacy and how secure they really are.
How is a Hand and Finger Geometry Scanner Used?
This type of technology is commonly used in large populations of people that need to be scanned in frequently. Places like factories, warehouses, storage facilities, etc., that employ large amounts of people and need to maintain a certain level of security benefit from using hand and finger geometry scanning. It's more reliable and secure than paper or card systems.

Fingerprint Lock
We all have unique fingerprints, so it makes sense that they can be used as a security measure. Fingerprint lock technology only gives access if the person with the correct fingerprint presses it. Each finerprint has ridges and valleys that are different than anyone else; the fingerprint lock keeps a record of these, especially where the ridges and valleys meet (minutiae). The lock is usually a smooth surface so the person can press their finger or thumb to it to be read.
Pros and Cons of Fingerprint Lock
The nice thing about fingerprint locks is that they don't require a key, which can be stolen or lost. Many times, depending on the device, multiple fingerprints can be entered in, so everyone in the family can access the safe, or whatever is locked using the fingerprint lock.
Some don't prefer fingerprint locks due to it not being touchless, meaning germs can be spread especially if it's used in a public setting. Fingerprint locks are notorious for not being especially reliable, and you typically need to place your finger or thumb precisely for it to be read.
How is a Fingerprint Lock Used?
Biometric fingerprint locks can be used to gain access to a business, an apartment complex, government agencies, and mobile phones.
Difference Between a Hand and Finger Geometry Scanner and a Fingerprint Lock
A hand and finger geometry scanner is not dealing with fingerprints at all. While it does scan all of the fingers, it does not analyze any of the fingerprints.[3] The hand and finger geometry scanner is simply dealing with the size of the hand, the length and width of each finger, and the shape of the hand as a result of the finger sizes.[4]
A fingerprint lock, on the other hand (no pun intended), does not deal whatsoever with the size or shape of the hand or fingers, but rather picks up and analyzes the fingerprint of one particular finger. (Although most fingerprint locks can register more than one fingerprint to allow access to more than one person— or more than one finger of the same person— they still deal with only one fingerprint at a time).
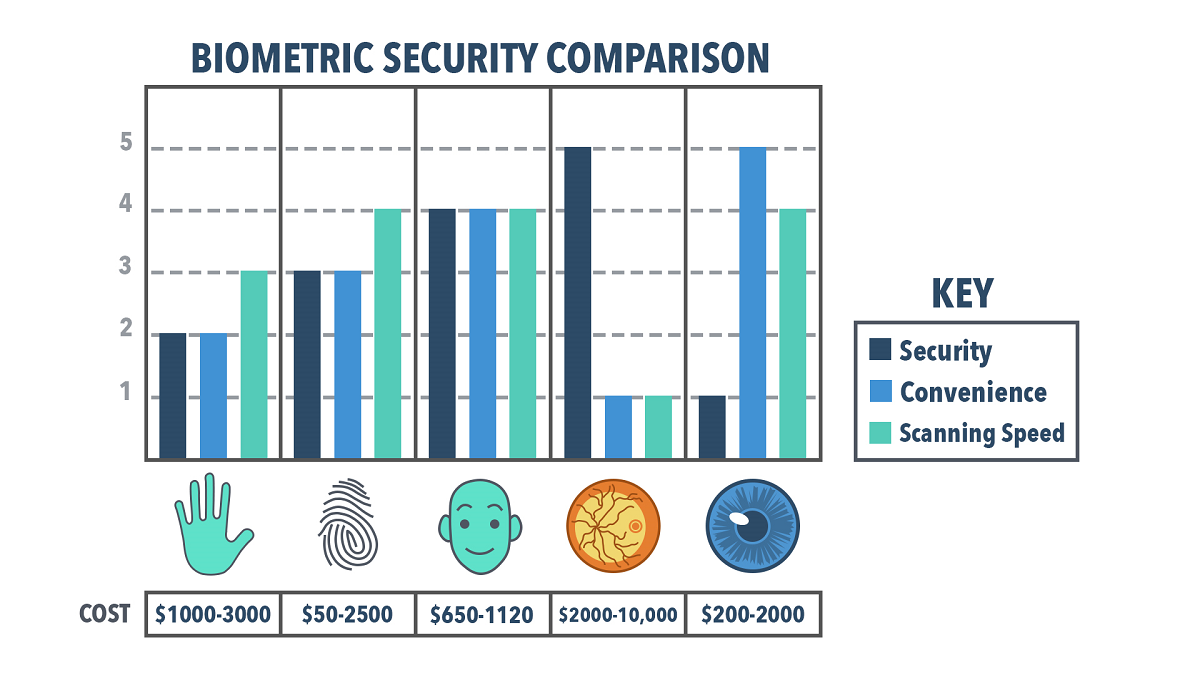
Which Type of Biometric Security is the Most Reliable?
Humans change over time, particularly very young humans or very old humans, but really all of us are subject to physical changes. So if we’re constantly changing, which type of biometric security is the most stable and able to account for these changes?
Hand geometry scanners and face scanners are the least reliable biometrics because both hands and faces can change size or shape significantly in a fairly short window of time due to routine events such as weight gain or loss.[3] However, this lack of total reliability does not make hand and face scanners useless in everyday situations. For example, many workplaces use hand geometry scanners for their clock in/out systems in lieu of ID cards. In the case of significant hand changes due to weight gain, weight loss, or pregnancy, these workplaces simply re-enroll that employee, or take a new base-scan of their hand.[3] Because the stakes of clocking in or out of work are relatively low (and ultimately correctable by a supervisor), the chances of a hand shape changing are not a deterrent for workplace use of a hand geometry scanner.
Fingerprint scanners are quite a bit more common than hand geometry scanners, possibly because fingerprints tend to be more stable than hand geometry. Fingerprints can change over time, but they change much less easily than hand geometry— i.e. a fingerprint will change if a person gets a cut that scars across the pad of the finger in question, or, more dramatically, a fingerprint will no longer be an effective means of authentication if a person loses their finger.[7] More common than drastic finger alteration— but equally problematic — is the presence of dirt, grease, or oil on the fingers, which disrupts the fingerprinting process and makes it difficult— if not impossible— to authenticate or identify a person.[7]
The retina cannot be affected by dirt or grease, since it resides inside of the eyeball. However, the retina can change over time as a result of a number of health issues, including diabetes and glaucoma.[5] These diseases are less likely than finger scars. Additionally, assuming that a person’s finger did not change and a person’s retina did not change, retinal scanning would be the more reliable biometric because retinal scanners take in more detail than fingerprint scanners, meaning that they are much less likely to return false accepts. However, as a result of the retina changing in response to quite a few health issues, retinal scanning is not perfectly reliable.[5]
Iris scanning— considered “to be ten times more accurate than fingerprinting”[1] is the most reliable biometric currently available. While the iris is plainly visible on the outside of the body, it is technically an internal organ because it is protected behind the cornea.[5] Since the iris is technically internal, it is not more likely than the retina to pick up dirt or debris. However, unlike the retina, the iris does not change with diseases such as glaucoma or diabetes.[5] While the iris can change during a person’s life, it tends to be stable after the age of one or two, and even if it does change it tends to be stable for at least a decade at a time.

Which Type of Biometric Security is Easiest to Trick?
On a first consideration, biometric security seems so much safer and so much more secure than passcode-protected security: somebody could figure out my passcode, but nobody has my finger, or my retina, or my iris. Unfortunately, a determined hacker or intruder can break even biometric security.
You may have seen the movie National Treasure,[8] in which Ben Gates (Nicolas Cage) steals both a fingerprint and a passcode from Dr. Abigail Chase (Diane Kruger) in order to gain her researcher access and steal the Declaration of Independence (certainly a document which should be impossible to steal).
So is it easier for Gates to steal Dr. Chase’s fingerprint or her passcode? Seemingly Dr. Chase’s fingerprint, which he lifts off of a champagne glass at the gala. In order to guess her passcode, Gates sends Dr. Chase a valuable gift, which he has coated in a chemical that shows in neon green under black light. He then can see which keys she hit on the passcode keyboard, and runs the letters through a passcode-breaking program, which still doesn’t guess the passcode. Luckily for Gates, he and Dr. Chase share a deep enthusiasm for history, which allows him to guess that her passcode is ‘Valley Forge’. It seems that the moral of this story is that you should not accept gifts from practical strangers, even (or perhaps especially) if they are nice gifts (which is a good lesson— don’t accept gifts from strangers!). However, had Dr. Chase not accepted the gift— and had the Declaration been protected only by a fingerprint lock, Gates could still have stolen the Declaration of Independence.
It is true that a passcode-breaking algorithm will eventually, given infinite guesses, find a passcode. However, eventually doesn’t really matter if it takes an unreasonably long time to guess correctly, and if you don’t write down a passcode anywhere or re-use a passcode anywhere, and you use a strong passcode, it can take millions, billions, trillions, or even more years for a computer to guess your password. The other trick is that your password has to be random enough that another human couldn’t easily guess it. (So ‘Valley Forge’ was a bad choice for Dr. Abigail Chase because it is a known fact that she is a big history geek, making it a relatively easy password to guess, especially given that Ben Gates knew which letters she had used).
The other consequence of biometric security is that if a thief or hacker steals your biometric information, you can’t change it the way that you can change a passcode.[9] Of course, most biometric security systems claim to store only ID patterns made from biometric information, and not the information itself, but Claire Gartland explains that “the growing rate of data breaches in [the banking] industry casts doubts on those kinds of promises” in a 2016 New York Times article.[9]. However, even assuming that companies don’t store biometric information, this safeguard does not fix the danger of thieves stealing actual biometric matter.
Originally, researchers were fairly confident that the iris of a dead person would not work in an iris scan because the blood vessels would deteriorate too quickly. However, later studies found that the iris of a dead person could work on an iris scanner for at least a few days after the person had died.[10] That being said, the likelihood of a thief killing a person and using their dead eyeball to break into their security is thankfully low— unless that person has access to something particularly valuable— say a lot of money, or something of great national or scientific value. Luckily, “researchers have trained a machine-vision system to tell the difference between dead irises and live ones” according to a 2018 article in the MIT Technology Review.[11]
Even though researchers have now solved the issue of a dead person’s iris working on an iris scanner, this issue highlights an important point in debates about biometric security: it’s still relatively new technology, and there may be problems that we do not yet understand or have not yet anticipated.
Is Biometric Security a Good Idea?
That being said, a lot of us use biometric security every day. Many of us have fingerprint locks on our phones or laptops, or even face or iris scanners.[12][13] More and more people have biometric gun safes (which usually work based on fingerprint locks).[14] Most of these biometric security devices are backed up with the option to have a PIN or passcode, in case the biometric ID fails (which it somewhat often does). A lot of biometric gun safes are backed up with a physical key rather than a passcode, which is supposed to make it more difficult for the owner’s children to gain access to the guns.[15]
For these types of personal things— things to which, in most cases, hackers and thieves are not actively trying to gain access— biometric security vs a traditional PIN or passcode is a matter of personal preference. However, sometimes the stakes are higher with these items than other times.

Are Biometric Gun Safes a Good Idea?
Most biometric gun safes are intended to make a personal handgun easier and quicker to access in the dark in the case of a home intruder.[15][16] Ideally, a person can use their fingerprint to unlock the gun safe, saving them the time and noise of trying to enter a PIN or use a physical key. However, the fingerprint locks on biometric gun safes can be just as unreliable as any other fingerprint lock, meaning that if the finger is at the wrong angle, the safe will likely not open; if the finger is dirty, the safe may not open; and if there are too many fingerprints stored in the program, the safe may take longer than anticipated to open.[15]
Since biometric gun safes tend to have a backup option (usually a physical key), there is probably no harm in having the option of using a fingerprint lock to open the safe, assuming that the user always keeps the backup option handy.

Which is Better to Lock Your Phone: PIN or a Biometric System?
In the case of our phones and computers, security isn’t a massive issue for the average person: we just want to keep nosy friends— or strangers, in the event that our phones are lost or stolen— out of our business. However, phone and computer security becomes a much more serious concern for people who have sensitive information, such as company business, sensitive contact information, or other information that would be problematic if it got out.[17]
Additionally, there has been some debate about whether a judge can order a person to open their device using a biometric method. While passcodes have been ruled to be protected by fifth amendment rights, biometric information does not have the same stable legal protection, since it is a relatively new technology and the laws have not yet caught up. The current ruling is that a judge cannot order a person to open a device with a biometric method, but this ruling is fairly new and not yet set in stone.[18][19]

Biometrics and Home Security
Imagine having a facial-recognition-equipped security camera on your front porch and a few more around the other entrances to your home; in the case of a break in, your system shoots you a text and tells you who broke in, where they live, and how many other crimes they have recently committed. It would be cool, right?
Luckily for your wallet, you can get the same net-effect with a YI camera and a Cove security system. While the Cove system won’t tell you immediately who is breaking into your home, it will tell you that there is a break-in, and the police will find the criminal later, based on the footage from your YI camera.
As cool as it looks, current biometric technology does not necessarily provide better security than traditional PIN, passcode, sensor, or camera methods. A determined criminal can work their way into almost any system, but that doesn’t mean you should give up on securing your home and your items! The Cove security system provides you with all of the important features of home security, at the low monitoring cost of $15 per month with no contract attached! With that kind of deal, you don’t need biometric home security!
Ready to be more secure at home? Click below to take our quiz and see what kinds of products we recommend to monitor your home. Equipment will be yours, and we never require contracts for monthly monitoring.

References:
- Chris Woodford, “Iris Scans”, https://www.explainthatstuff.com/how-iris-scans-work.html
- Richard P. Wildes, “Iris Recognition: An Emerging Biometric Technology”,
- Capture it, “Pros and cons of the Biometric Handscanner”,
- Tracy V. Wilson, “How Biometrics Works: Hand and Finger Geometry”,
- John Trader, “Iris Recognition vs. Retina Scanning — What are the Differences?”,
- Andrew Aarons, “What Are the Dangers of Retinal Scanners?”,
- Iridian Technologies, “Biometric Comparison Guide”,
- Jon Turteltaub, National Treasure, 2004. 9. Claire Gartland, “Biometrics Are a Grave Threat to Privacy”,
- Eliza Strickland, “Biometrics Researcher Asks: Is That Eyeball Dead or Alive?”,
- Emerging Technology from the arXiv, “Iris scanner can distinguish dead eyeballs from living ones”,
- Amy Nordrum, “New Samsung Galaxy S8 Unlocks with Facial Recognition, Iris Scanning”,
- Aatif Sulleyman, “Face ID or Touch ID? Apple’s new iPhones could upset a lot of people”,
- Gunvault, “Biometric Gun Lock Technology”,
- Shooting & Safety, “5 Best Biometric Gun Safes in 2019”,
- GunVault, “Biometric Gun Safes”,
- Simon Batt, “Should You Use a Fingerprint or a PIN to Lock Your Phone?”,
- Cameron Summerson, “U.S. Judge Rules Fingerprint, Face Unlock Are Protected Just Like Passwords”,
- Thomas Brewster, “Feds Can’t Force You to Unlock Your iPhone With Finger Or Face, Judge Rules”,
Ready to get started?
Take this short quiz to build your customized system today!
Takes less than a minute


